SSO (Single Sign-On) can be implemented using an identity provider to authenticate a TrialMaster user. The SSO URL for the SSO login must be specified in AnjuEDC and SSO must be enabled in the configuration settings. (Multiple SSO URLs can be specified.) Each URL is given a name and has an internal id. The authentication authority is specified per organization to avoid exposing authentication authority across clients in the shared environment.
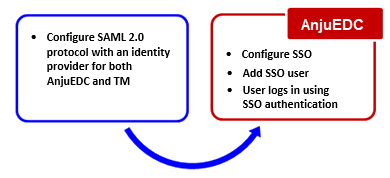
The following figure illustrates the SSO configuration process. As shown in this figure, you must first configure SAML 2.0 with an identity provider for both the AnjuEDC and TrialMaster applications. Then from AnjuEDC, configure the SSO and add the SSO user. The user can then log in to AnjuEDC using the SSO authentication. (TrialMaster and AnjuEDC support SSO authentication through SAML 2.0.)
To configure SSO:
1. Use one of the following identity providers to configure the SAML 2.0 protocol:
· Microsoft’s Active Directory Federation Services (AD FS) server (See Configure AD FS with SAML 2.0 Protocol.)
· OKTA identity cloud (See Configure OKTA with SAML 2.0 Protocol.)
· Azure Active Directory (See Configure Azure Active Directory with SAML 2.0 Protocol)
2. Configure SSO authentication URLs.
4. Add the SSO user.